用于确认某个升级包是否被安装。
一、ubuntu、debian系列:
/var/log/dpkg.log
/var/log/apt/history.log 等
# cat /var/log/dpkg.log|grep upgrade
2024-07-01 11:00:54 upgrade openssh-sftp-server:amd64 1:8.9p1-3ubuntu0.7 1:8.9p1-3ubuntu0.10
2024-07-01 11:00:55 upgrade openssh-server:amd64 1:8.9p1-3ubuntu0.7 1:8.9p1-3ubuntu0.10
2024-07-01 11:00:56 upgrade openssh-client:amd64 1:8.9p1-3ubuntu0.7 1:8.9p1-3ubuntu0.10
2024-07-01 11:00:57 upgrade ssh:all 1:8.9p1-3ubuntu0.7 1:8.9p1-3ubuntu0.10
# cat /var/log/apt/history.log
Start-Date: 2024-07-01 11:00:54
Commandline: apt-get -o Dpkg::Options::=--force-confdef -o Dpkg::Options::=--force-confold --ignore-missing -fy upgrade
Upgrade: openssh-client:amd64 (1:8.9p1-3ubuntu0.7, 1:8.9p1-3ubuntu0.10), ssh:amd64 (1:8.9p1-3ubuntu0.7, 1:8.9p1-3ubuntu0.10), openssh-server:amd64 (1:8.9p1-3ubuntu0.7, 1:8.9p1-3ubuntu0.10), openssh-sftp-server:amd64 (1:8.9p1-3ubuntu0.7, 1:8.9p1-3ubuntu0.10)
End-Date: 2024-07-01 11:01:02
# ls -l /usr/sbin/sshd
-rwxr-xr-x 1 root root 917192 Jun 26 13:11 /usr/sbin/sshd
# cat /etc/os-release
PRETTY_NAME="Ubuntu 22.04.4 LTS"
NAME="Ubuntu"
VERSION_ID="22.04"
VERSION="22.04.4 LTS (Jammy Jellyfish)"
二、CentOS、Redhat系列
/var/log/yum.log
# cat /var/log/yum.log|grep ssh
Jun 03 11:08:31 Updated: libssh2-1.8.0-4.el7_9.1.x86_64
Jun 03 11:08:59 Updated: openssh-7.4p1-23.el7_9.x86_64
Jun 03 11:09:07 Updated: openssh-server-7.4p1-23.el7_9.x86_64
Jun 03 11:09:08 Updated: openssh-clients-7.4p1-23.el7_9.x86_64
# yum history
ID | Command line | Date and time | Action(s) | Altered
------------------------------------------------------------------------------------------------------------
102 | -y update | 2024-07-03 12:00 | C, E, I, U | 13
101 | -y update | 2024-06-06 07:00 | C, E, I, U | 15
100 | -y update | 2024-05-31 06:00 | Upgrade | 3
99 | -y update | 2024-05-30 18:00 | Upgrade | 1
98 | -y update | 2024-05-28 23:00 | C, E, I, U | 211 EE
三、AlmaLinux
# grep ssh /var/log/dnf.rpm.log
2024-05-28T23:01:14+0800 SUBDEBUG Upgrade: openssh-8.0p1-24.el8.x86_64
2024-05-28T23:01:34+0800 SUBDEBUG Upgrade: libssh-config-0.9.6-14.el8.noarch
2024-05-28T23:01:34+0800 SUBDEBUG Upgrade: libssh-0.9.6-14.el8.x86_64
2024-05-28T23:01:59+0800 SUBDEBUG Upgrade: openssh-server-8.0p1-24.el8.x86_64
2024-05-28T23:01:59+0800 INFO warning: /etc/ssh/sshd_config created as /etc/ssh/sshd_config.rpmnew
2024-05-28T23:01:59+0800 SUBDEBUG Upgrade: openssh-clients-8.0p1-24.el8.x86_64
2024-05-28T23:02:05+0800 SUBDEBUG Upgraded: openssh-server-8.0p1-19.el8_9.2.x86_64
2024-05-28T23:02:05+0800 SUBDEBUG Upgraded: openssh-clients-8.0p1-19.el8_9.2.x86_64
2024-05-28T23:02:06+0800 SUBDEBUG Upgraded: openssh-8.0p1-19.el8_9.2.x86_64
2024-05-28T23:02:19+0800 SUBDEBUG Upgraded: libssh-0.9.6-13.el8_9.x86_64
2024-05-28T23:02:20+0800 SUBDEBUG Upgraded: libssh-config-0.9.6-13.el8_9.noarch
# cat /var/log/dnf.log
2024-07-03T19:00:02+0800 INFO --- logging initialized ---
2024-07-03T19:00:02+0800 DDEBUG timer: config: 10 ms
2024-07-03T19:00:02+0800 DEBUG Loaded plugins: builddep, changelog, config-manager, copr, debug, debuginfo-i
nstall, download, generate_completion_cache, groups-manager, needs-restarting, playground, repoclosure, repo
diff, repograph, repomanage, reposync, system-upgrade
2024-07-03T19:00:02+0800 DEBUG YUM version: 4.7.0
2024-07-03T19:00:02+0800 DDEBUG Command: yum -y update
参考:
https://blog.csdn.net/weixin_32929205/article/details/116712520
https://superuser.com/questions/147857/how-to-view-history-of-yum-commands-update-install-remove
OpenSSH远程代码执行漏洞 (CVE-2024-6387) 安全风险通告
https://www.secrss.com/articles/67636?app=1
https://www.nodeseek.com/post-128284-1
影响版本:8.5p1 <= OpenSSH < 9.8p1
sshd升级后,大版本不变,后面的小版本号有变化
# ssh -V
原始版本:
OpenSSH_8.9p1 Ubuntu-3ubuntu0.6, OpenSSL 3.0.2 15 Mar 2022
此次更新后的版本:
OpenSSH_8.9p1 Ubuntu-3ubuntu0.10, OpenSSL 3.0.2 15 Mar 2022
更新完之后,sshd最新安全版本号如下:
Debian 12: 9.2p1-2+deb12u3
Ubuntu 22.04: 8.9p1-3ubuntu0.10
Ubuntu 24.04: 9.6p1-3ubuntu13.3
AlmaLinux 9: 8.7p1-38.el9.alma.2
Oracle Linux 9: 8.7p1-38.0.2.el9
https://www.ithome.com/0/779/000.htm
如果 OpenSSH 服务器无法立即更新,可在 sshd 配置文件中将 "LoginGraceTime" 设置为 0,但要注意这可能会使服务器遭受拒绝服务攻击。
Linux OS尽量选择LTS(长期支持 Long-term support)的版本,再安装中神通大地云控,因为大地云控的安全加固功能具备自动/强制系统升级的功能,一小时检查一次,能保证安全升级包第一时间安装到位,让黑客无机可乘:
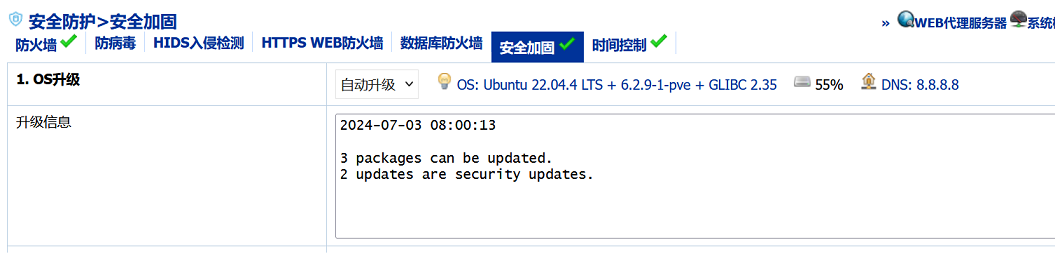

更多介绍:
http://www.trustcomputing.com.cn/cn/index.php/product/dns-url

下载地址:
http://www.trustcomputing.com.cn/bbs/viewthread.php?tid=1174
[
本帖最后由 linda 于 2024-7-4 14:25 编辑 ]